Identity and access management (IAM) is crucial for organizations, transforming their businesses with advanced digital processes and programs. Organizations from various industrial verticals need to stay abreast of the changing trends and advancing technologies in identity and access management. Digitization has transformed the business scenario and as a result, organizations are keen to keep abreast of the rapid advancement of technology in order to enhance their business and product sales.
Digital transformation has its own set of challenges, primarily in the form of security concerns and threats to data privacy, which makes IAM a crucial strategy for any business. Identity and access management can secure the right to use and control programs, systems and functions used by employers as well as employees.
One of the most rapidly evolving security systems, identity management or identity and access management, ensures access to different essential functions and vital resources by the right people in an organization. It is critical for IAM systems to grant access to the right people, at the right time and for the right reason. Hence, identity and access management is an asset as well as a liability to the organization. It is essential that businesses leaders understand that security definitions are constantly evolving. Hence, the identity access management tools installed across all critical points of an organization need to be updated as well as compatible with advanced devices and functionalities. All in all, adoption of the right type of IAM system is critical as it determines the strength of an organisation’s overall security strategy.
Identity and Access Management Strategy Essentials and Trends

Technology is evolving at a disruptive pace. This fact is evidenced by the rapid advancements across all technology niches but, in particular with the development of the tools & technologies available within identity and access management systems. Business leaders adopting the advanced IAM systems must address the interdependencies of diverse ecosystems and a multitude of business platforms. In doing so, they will improve their business’ agility and its ability to respond to security breaches and threats in real-time
Increased dependence on cloud services and internet of things (IoT) are the major threats to cybersecurity and data privacy. Hence, a rising number of organizations are raising their security budgets so that they can ensure the utmost security for all components within the organization. The importance of an organisations’ Identity and access management strategy cannot be overstated as it controls the occurrences of cyberattacks and internal security threats.
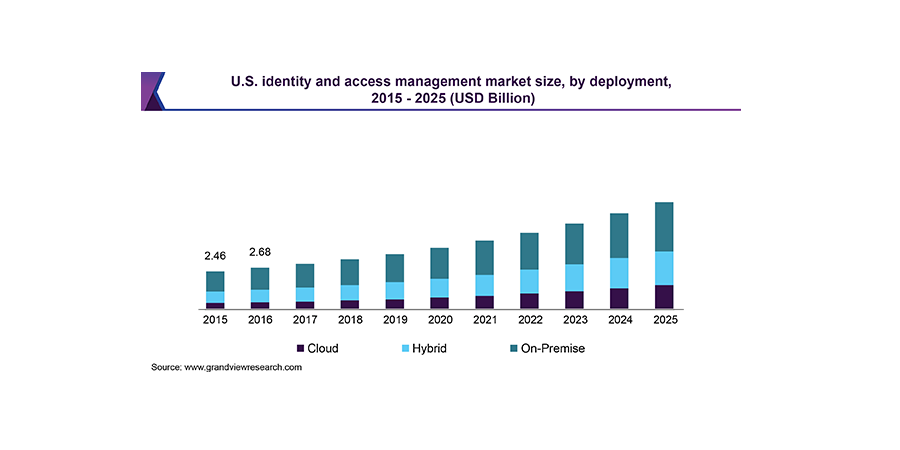
The majority of companies prefer on-premise IAM solutions, with a considerable percentage preferring to deploy a hybrid model - a combination of cloud and on-premise solutions. Hybrid solutions are particularly effective for mobile enterprises.
Technological developments in cloud-based Identity-as-a-Service (IDaaS) are forecast to prompt a major trend for innovation in the IAM solutions industry. The introduction of innovative solutions from vendors such as Centrify and Okta will also potentially, transform the security and threat management scenario for years to come. Identity and access management solutions associate all the activities taking place within a business ecosystem through a device or specific user. These solutions then keep a track of all the activities and create reports. The systems make use of single-sign-on (SSO) and other strong user authentication services for heightened security. Separate security protocols for applications, devices and networks is a major factor that the organizations need to consider while adopting IAM solutions.
Therefore, the key to effective implementation of digitization depends on development of real-time and easily accessible security and identity & access management solutions. It is essential for these solutions to be sharable throughout all components of a business ecosystem, namely, owners, partners and workforce. Technological advancements and trends like IoT, bring your own device (BYOD), and connected enterprise, IAM strategy should be identifiable across multiple domains. Hence, organizations need to be prepared for increased investments in research, hardware and manpower associated with this.
Some of the top trends observed in the global identity and access management market:
#1 GDPR
The recent General Data Protection Regulation (GDPR) legislation passed by the European Union (EU) was created to merge and fortify data security across the entire EU territory. US-based companies are also expected to pay additional attention to data governance, additional security for sensitive data, unstructured data and overall data distribution across processes.
#2 Identity Assurance
More than simple password management solutions, organizations today need enhanced security solutions that require decision-based identity assurance. While implementing these solutions the context is crucial while granting access requests for resources from particular employees or any other component of the organization. Identity assurance systems look for threat warnings and help organizations keep track of suspicious activities, generating notifications when access needs to be blocked or adding layers of enhanced security.
#3 Non-Stop Security
Modern day identity and access management solutions need to deliver results that are flexible, in real-time and uninterrupted. Organizations are spending time as well as money in developing technologies which adhere to the aforementioned prerequisites. It is essential for organizations to use IAM tools that provide seamless and continuous authentication. Identity and access management is a non-stop process, essential to protect the businesses from advanced threats and security protocols, despite the presence of next-gen firewalls across large organizations.
#4 Multi-Factor Authentication (MFA)
Multi-factor authentication is one of the most widely discussed areas of identity and access management industry. MFA can protect systems and programs from phishing. It requires different independent security or authentication methods that determine login, identity and access or other transactions. Multi-factor authentication requires the user to present two or more verifications or confirmations to prove identity. However, according to research, most current, multi-factor authentication programs still have loopholes and are in need of technological refinements.
#5 Identity API Management
One of the most revolutionary trends, identity application programming interface (API) management grants connection of cloud applications and people to give programmer-level access and audit trails to anyone trying to access API gateways. It involves gathering security intelligence from several trusted sources. Rising adoption of intelligence to boost interaction between API and applications is a boon to this IAM tool.
#6 Security Robotics
Increased use of robotics in identity and security management is another prominent trend observed by analysts. The security sector aims to use robotics to accomplish essential tasks in enterprise settings, including in the context of identity and access rights management. Digital IAM can be a real benefit for industries committed to innovation and topnotch security solutions. Robotic process automation (RPA) offers competitive edge to businesses and also accelerates productivity and accuracy.
Identity and Access Management Market Scenario

As per the market research report created by Grand View Research, the global identity and access management market will continue to witness healthy growth for the foreseeable future. According to the report, the market is poised to reach nearly US $22.68 billion by 2025., with increasing adoption of web-based applications expected to be the major market driver. Research and development and policy-based security compliance will further boost the IAM market. While audit management and cost containment will boost the adoption of identity management across industries for years to come.
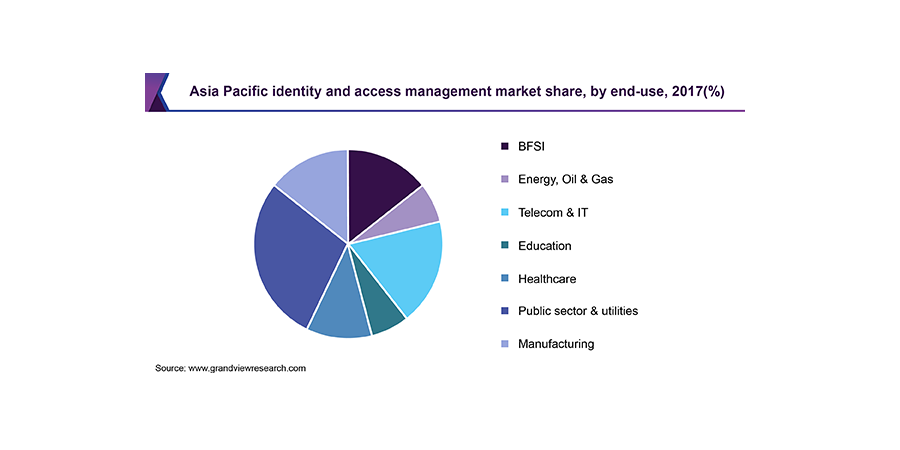
It is anticipated the BFSI segment will see the strongest exponential growth, in terms of adoption of IAM solutions, as security of consumer data is paramount.
Moving forward, there is a growing awareness of the availability of such security management solutions and large enterprises are spending increasingly hefty budgets on these solutions. Intensified compliance regulations from governments may further fuel demand for advanced IAM solutions. Developments in technology, coupled with increased adoption of automated business processes by emerging economies, are expected to generate business opportunities for the top market players including Dell Software, Oracle, IBM, Amazon Web Services, HP, HID Global Corporation, and OneLogin among others.
Major organizations operating in the global identity and access management are inclined towards research and development, innovations and product and technological advancements. Mergers and acquisitions (M&A) and business partnerships are used as the predominant business strategies among the top market participants. Research suggests that widespread adoption of cloud and mobile devices can create ample growth and investment opportunities for years to come.
Ironically, many of the top IAM vendors are in a vulnerable position, brought about by the constantly evolving security parameters, consumer requirements and technological developments. As a result, it is vital for them to stay on top of changing trends. Product innovation offering real-time upgrades can offer a safeguard against this scenario as well as driving further business opportunities. Additionally, it is anticipated that emerging economies will show a steady rise in their adoption rates of IAM solutions.
Major players in the global identity and access management market need to find solutions to escape the legacy manual processes. According to the experts, policy-based solutions such as cloud-based identity governance and administration (IGA) is unavoidable. Therefore, it is imperative to embrace a rational approach to access risk management, which will help them offer use-friendly IAM solutions to the end-users.
Author: Rutuja Jathar 
Author Bio:
Rutuja Jathar is a writer and editor with 9+ years of work experience. Currently leading a team of technical writers at Grand View Research, her passion for words and technology reflects in her contribution to developing and editing research information. She has also written numerous industry blogs and news features as a guest author. When not writing, she likes to stay informed about technological innovations and disruptions across all walks of life.
Contact Details:
Email: info-apac@grandviewresearch.com
Phone: 1-415-349-0058
LinkedIn: https://www.linkedin.com/company/grand-view-research/
Website: https://www.grandviewresearch.com/







